I set up an Active Directory domain for my HomeLab. I'm still learning a lot about Active Directory as it is such a large piece of software.
Configuring Active Directory
Installation was pretty simple and I'm not going to go over that as there is a vast amount of documentation available.
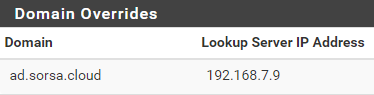
I should note though that as I wanted to keep pfSense as my DNS server, I set my Active Directory domain to ad.sorsa.cloud instead of the root of the domain. Then I configured a domain override into pfSense's DNS Resolver.
So Active Directory was working just fine. Using a windows machine I created a new user and made it a member of some groups. I also added my desktop SSH public key to the attribute altSecurityIdentities.
Making Linux play with Active Directory
The next step was making a Linux server join the domain.
I fired up an RHEL 8 VM and installed the following packages:
- sssd
- sssd-tools
- realmd
- oddjob
- oddjob-mkhomedir
- adcli
- samba-common
- samba-common-tools
- krb5-workstation
- openldap-clientsJoining the domain with realmd was really simple. realm join ad.sorsa.cloud and voilà! After authentication, the server was successfully added to the domain.
User home directory creation is handled by oddjob-mkhomedir and authentication is handled by SSSD.
Now by logging in with [email protected]@localhost I was able to access this new account!
Next, I added a rule like this to sudoers:
%Enterprise\ [email protected] ALL=(ALL:ALL) ALLNow all members of Enterprise Admins have sudo privilege on this machine.
Conclusion & Improvements
The next step I'm taking is automating the enrollment into the domain with ansible. I've already succeeded in this but haven't had the time to write a blog post about it.
Even though as I'm the only user of this homelab, I want to add more granular control for sudo access. I'm going to create a new group for every machine that is joined, ADMIN_hostname. Then define sudo rules for this group via templating.

